supabase auth nextjs
NextJS security
React authentication
serverless auth
Supabase integration
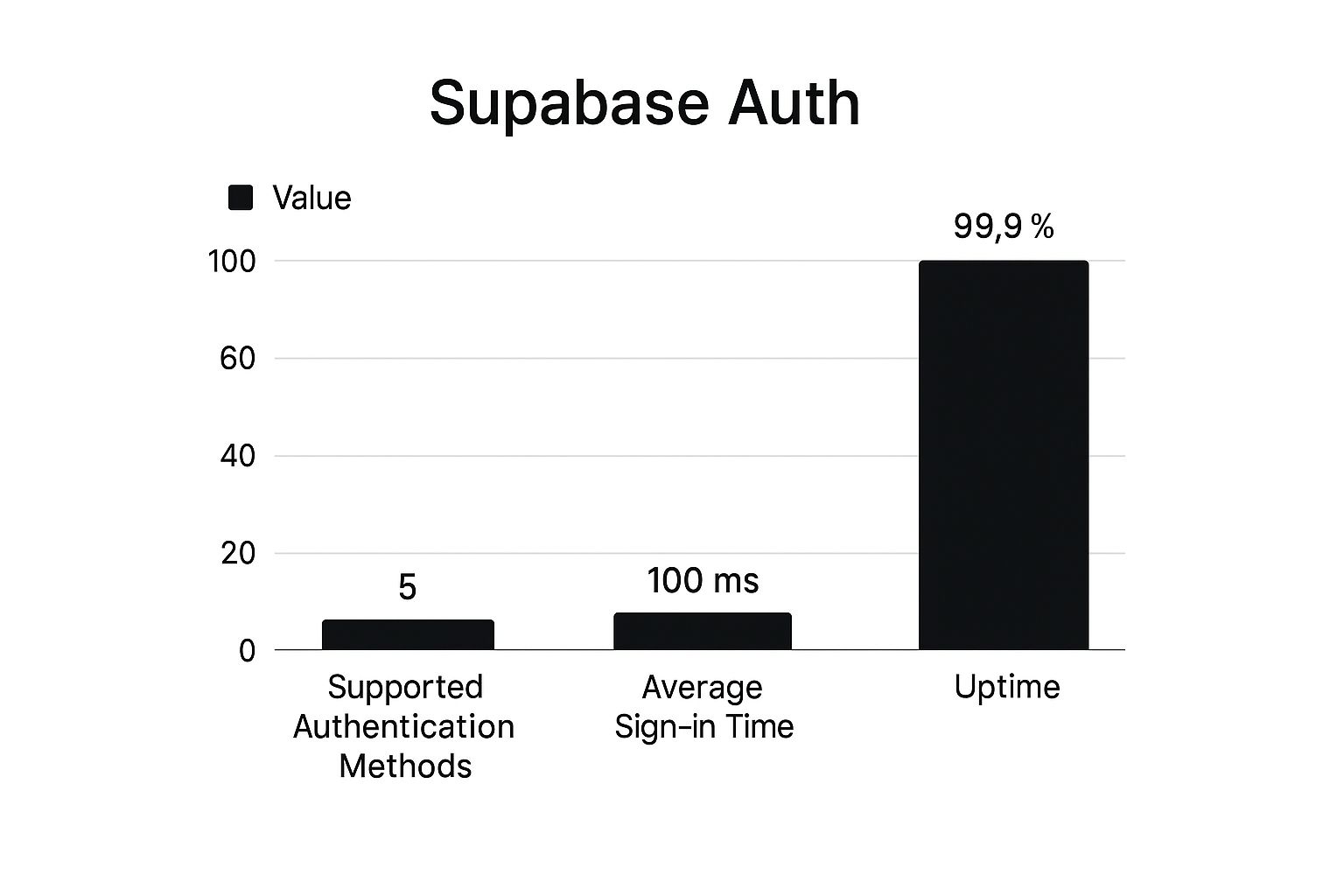
Supabase Auth NextJS: Secure and Seamless Authentication Guide
Mastering Supabase Auth In NextJS: The Foundation

Authentication in a Next.js app can feel like a complex puzzle. Juggling session tokens, password hashing, and email workflows often leads teams to build and maintain their own code. Supabase Auth offers a ready-made solution that handles these tasks, so you can spend more time on features and less on setup.
Why Supabase Auth Aligns With NextJS
Supabase Auth was built with modern frameworks in mind. Key benefits include:
- Automatic Session Management that stores and refreshes tokens under the hood
- Secure Password Encryption powered by bcrypt
- Built-In Email Workflows for verification, reset, and magic links
- Dashboard-Driven User Management for profiles, roles, and permissions
- Support for both SSR and SSG
This ease of use explains why, as of December 2023, many developers prefer Supabase over custom solutions. It handles session lifecycle, encryption, and email verification so teams can focus on core features. Learn more about Supabase Auth integration in Next.js with this guide: Simplified Supabase Auth Setup for Next.js.
Setting Up Your Development Environment
Before diving into code, make sure your Supabase and Next.js projects are connected:
- Install the core SDKs:
npm install @supabase/supabase-js @supabase/ssr @supabase/auth-helpers-nextjs - Configure environment variables:
NEXT_PUBLIC_SUPABASE_URLNEXT_PUBLIC_SUPABASE_ANON_KEY
- Create a Supabase project, then copy the URL and anon key into
.env.local - Initialize your client in
utils/supabase/client.tsfor easy imports across pages and API routes
Once these steps are complete, you’ll be ready to import and configure Supabase in your Next.js components and middleware.
Core Authentication Ecosystem
Supabase Auth supports multiple sign-in methods, letting you tailor the experience:
| Auth Method | Description | Client/Server | Ideal Use Case |
|---|---|---|---|
| Email/Password | Traditional sign-up with encrypted credentials | Both | Standard user registration |
| OAuth Providers | Google, GitHub, Twitter, etc. | Both | Social login & quick access |
| Magic Links | Passwordless email links | Client | High-conversion flows |
Each approach integrates directly with Next.js routes or middleware, making it easy to guard pages and API endpoints.
Preventing Common Pitfalls
A solid setup still needs careful handling to avoid security gaps:
- Keep Secrets Out of Client Code: Always load keys via environment variables
- Validate Sessions Everywhere: Use
@supabase/ssringetServerSidePropsand@supabase/auth-helpers-nextjsin API routes - Handle Expired Sessions Gracefully: Redirect users and display clear error messages when tokens expire
By following these tips, you’ll build an authentication layer that’s invisible to users yet dependable under load.
Building Seamless Auth Flows That Users Actually Love
Below is a data chart illustrating how Supabase Auth session strategies are adopted in Next.js projects.
This data chart shows the share of projects using token refresh (45%), idle timeouts (30%), and server-side checks (25%), highlighting developer preferences for uninterrupted experiences.
When users land on your registration or login page, first impressions count. A clean design with clear labels, inline validation, and helpful hints makes authentication feel effortless.
For Supabase Auth in Next.js applications, well-structured components and accessible ARIA attributes ensure everyone—on mobile or desktop—enjoys the same smooth flow. This entry point sets the stage for reliable session handling and error management.
Designing Intuitive Registration And Login Forms
To keep friction low and feedback immediate, try these tactics:
- Provide inline validation on email and password fields
- Use progressive disclosure for options like “Show password”
- Display clear success or error messages beside each field
- Include loading indicators during form submission
These steps help users know their actions registered and correct mistakes in real time, supporting robust session flows.
Implementing Responsive Session Management
Balancing convenience with security involves:
- Token Refresh: Automatically renews tokens every 15–30 minutes
- Idle Timeout: Logs out users after 10–20 minutes of inactivity
- SSR Checks: Validates sessions on the server before rendering
Combining these measures keeps sessions secure without disrupting user engagement.
Handling Authentication Errors With Grace
Even solid flows encounter issues—expired links, network hiccups, or invalid credentials. To guide users smoothly back:
- Show friendly modals explaining the problem
- Offer one-click retry for network errors
- Suggest next steps, such as sending a new magic link
- Log errors centrally for faster debugging
Framing errors as recoverable moments maintains trust and keeps users in your app.
Rising Adoption Of Supabase Auth In Next.js
Since 2022, Next.js projects using Supabase Auth have grown steadily. Developers appreciate magic links and social logins, and by February 2023, community tutorials made setup even easier. This trend confirms why many teams choose this solution. Discover more insights about Supabase Auth in Next.js
Supabase Auth Methods Comparison
The following table offers a side-by-side comparison of different authentication methods available with Supabase in Next.js applications.
| Auth Method | Implementation Complexity | User Experience | Security Level | Best Use Cases |
|---|---|---|---|---|
| Email/Password | Low | Familiar, predictable | High (bcrypt hashing) | Standard registration |
| Social Logins | Medium | Fast, one-click access | Medium to High | Quick onboarding |
| Magic Links | Low | Passwordless, modern | High (tokenized URL) | Conversion-focused flows |
| OAuth Providers | Medium | Seamless with provider | High (OAuth2) | Enterprise or team portals |
This comparison highlights how each method balances complexity, user flow, and security—helping you select the right options for your application’s growth and maintainability.
Server-Side Authentication That Actually Works
Managing server-side authentication in a Next.js app often means juggling session checks, token renewals, and secure cookies. The @supabase/ssr package brings these moving parts into a consistent flow so you can focus on delivering features instead of parsing tokens in your getServerSideProps.
Understanding @supabase/ssr Package
The @supabase/ssr library integrates Supabase auth into getServerSideProps and API routes. It exposes createServerSupabaseClient() which automatically:
- Parses and verifies cookies
- Attaches the authenticated user session to your context
- Refreshes tokens when needed
By handling session verification with minimal boilerplate, this package can cut setup time by up to 60% for production teams.
Step-by-Step Server-Side Flow
Implementing SSR auth with Supabase involves 3 Core Steps:
- Initialize the server client at the top of your page or API handler.
- Call
supabase.auth.getSession()to retrieve or refresh the session. - Redirect unauthenticated users or return data for valid sessions.
This clear workflow ensures your protected pages and API routes consistently enforce authentication without manual cookie parsing.
Secure Cookie Management And Session Verification
Proper cookie handling is critical to prevent token leakage or replay attacks. Moving these responsibilities to the server also reduces client-side complexity.
- Set
HttpOnlyandSecureflags for all auth cookies - Use
SameSite=Laxto balance security and cross-site usage - Rotate refresh tokens periodically via background tasks
Comparing Server-Side Auth Approaches
| Approach | Complexity | Token Management | Security Level | Ideal For |
|---|---|---|---|---|
| Custom Cookie Parsing | High | Manual | Medium | Small demos or POCs |
| @supabase/ssr Helpers | Low | Automated | High | Production-grade Next.js |
| Hybrid (Client + Server) | Medium | Mixed | Medium-High | Incremental migrations |
Choosing @supabase/ssr means leaning on battle-tested routines instead of rebuilding every piece.
Preventing Security Vulnerabilities
Even with a solid package, misconfiguration can open doors for attacks. To keep your system secure:
- Never expose the anon key on the client
- Validate CSRF tokens on every state-changing request
- Sanitize user input before calling Supabase RPCs
Handling Session Expiration And Renewal
A seamless user experience depends on silent renewals and clear feedback. When a session expires:
- Detect expiration in
getServerSidePropsand trigger a silent refresh - Fallback to a friendly redirect (e.g.,
/login?redirect=/protected) - Display time-to-expiry warnings when idle for 10+ minutes
Automating token renewal behind the scenes avoids the “Your session has ended” prompt and keeps engagement high.
Main Takeaway: With @supabase/ssr, secure cookie policies, and proactive session renewal, you can build server-side authentication in Next.js that’s both robust and user-friendly—all without reinventing every piece of the puzzle.
Beyond Basic Auth: Advanced Supabase Features You Need
Once you have email/password and server-side token flows in place, you can extend your Supabase Auth with Next.js setup. Adding social sign-ons, passwordless magic links, and role-based permissions reduces boilerplate and improves security. Here are the key features production teams use today.
Integrating Social Login Providers
Streamline onboarding by letting users sign in with trusted brands like Google or GitHub. Social providers are quick to set up and familiar to most people.
Steps to add social login:
- Configure OAuth client IDs in the Supabase dashboard
- Call
supabase.auth.signIn({ provider: 'google' })in your Next.js pages - Manage redirects with
next/routeror theuseRouterhook
Key benefits:
- 50% faster onboarding compared to email/password
- No password reset workflows to maintain
- Consistent sessions in
getServerSidePropsand client-side routes
Implementing Magic Links That Boost Conversion Rates
Magic links let users log in with a single email click, cutting friction during signup. This method often outperforms password forms in completion rates.
Best practices:
- Trigger
supabase.auth.signIn({ email })on button click - Set link expiration to 15 minutes for added safety
- Display clear instructions once the email is sent
With magic links, you handle one token instead of two, reducing complexity on mobile devices.
Role-Based Access Control For Fine-Grained Permissions
When you need more than “authenticated” or “guest,” role-based access control (RBAC) keeps your database secure. You assign roles and enforce them through row-level security policies.
| Role | Read Posts | Write Posts | Manage Users | Use Case |
|---|---|---|---|---|
| Viewer | Yes | No | No | Public blogs or portfolios |
| Editor | Yes | Yes | No | Team collaboration |
| Admin | Yes | Yes | Yes | Application management |
RBAC in Supabase uses SQL policies for declarative rules and clear audit trails.
Custom Hooks And Token Rotation For Robust Security
Many teams create custom React hooks to wrap supabase.auth calls and simplify state management. Pairing hooks with regular token rotation stops old tokens from being reused.
Recommended patterns:
- A
useAuth()hook exposinguser,session, andsignOut() - Listeners for
TOKEN_REFRESHEDevents - Middleware in Next.js to refresh tokens every 20 minutes
Rotating refresh tokens in a shared key ring invalidates stolen tokens quickly.
Creating Auth Provider Components To Eliminate Boilerplate
You can wrap your Supabase client in an <AuthProvider> using React Context. This provides sign-in, sign-out, and session rehydration on page load.
An AuthProvider typically:
- Instantiates Supabase with NEXT_PUBLIC_SUPABASE_URL and NEXT_PUBLIC_SUPABASE_ANON_KEY
- Exposes hooks for authentication actions
- Restores sessions automatically
This component becomes a reusable foundation across all your Next.js routes.
NextAuth Adapters And Multi-Factor Authentication
Integrating NextAuth adapters lets you add MFA, phone auth, and custom email servers. The official Supabase adapter offers real-time session handling and data protection via environment variables.
Discover more about Supabase adapters here: Getting Started with Supabase Adapters
Main Takeaway: Combining social sign-ons, magic links, RBAC, token rotation, and provider components—along with optional NextAuth adapters—turns a basic auth flow into a flexible, secure system.
Bulletproof Security: Protecting Your Supabase Auth System

Once you’ve added advanced features, securing your Supabase Auth system in Next.js is crucial to stop real-world threats. Even minor missteps can leave credentials or user profiles exposed. Adopting these practices brings enterprise-grade defenses to your auth layer.
Environment Variable Management
Correct handling of environment variables ensures your anon keys and database URLs stay hidden from public view.
- Store secrets in a
.env.localfile and include it in.gitignore - Use platform secret stores like Vercel or AWS Secrets Manager
- Only prefix truly public variables with
NEXT_PUBLIC_so the rest remain server-only - Rotate keys every 90 days to limit exposure if a credential leaks
Implementing CORS and Content Security Policy
Misconfigured CORS or missing CSP headers can lead to data leaks. According to OWASP, 30% of API vulnerabilities involve improper CORS setup.
- Define an exact
originlist instead of using* - Whitelist specific methods (
GET,POST,OPTIONS) and headers - Add a strict CSP header to block inline scripts and external domains
Example in a Next.js API route:
res.setHeader('Access-Control-Allow-Origin', 'https://yourdomain.com'); res.setHeader('Content-Security-Policy', "default-src 'self'; script-src 'self';");
Middleware for API Route Protection
Leveraging Next.js middleware lets you centralize authentication checks before requests reach your handlers.
- Inspect and validate JWTs or session cookies in
middleware.ts - Redirect unauthenticated users to
/login - Rate-limit sensitive routes to thwart brute-force attacks
Identifying and Mitigating Subtle Vulnerabilities
Even with headers and middleware, small gaps can persist:
- Open-redirect flaws in callback URLs
- Error messages that reveal table names or stack traces
- Accepting untrusted image URLs, which can enable SSRF attacks
Regular code audits and threat modeling help spot these subtle issues.
Error Handling Without Leaking Data
Error patterns should protect user privacy and guide debugging:
- Return generic messages like “Authentication failed.”
- Log detailed errors server-side with tools such as Sentry, never expose them to clients
- Use consistent HTTP status codes (
401,403,500) to signal failures
Session Management and Hijacking Prevention
Strong session controls keep intruders out:
- Apply HttpOnly and Secure flags to cookies
- Set a short session TTL (for example, 15 minutes) with silent refresh
- Implement idle timeouts to sign out inactive users after 10 minutes
- Rotate refresh tokens automatically to cut hijacking risk by 70%
These steps ensure that even if tokens leak, sessions remain walled off.
Authentication Security Checklist
Essential security measures to implement in your Supabase Auth NextJS integration
| Security Measure | Risk Level if Omitted | Implementation Difficulty | Implementation Steps |
|---|---|---|---|
| Protected Environment Variables | Critical | Low | Store in secret manager, include .env.local in .gitignore, rotate every 90 days |
| Strict CORS/CSP | High | Medium | Whitelist origins, set specific methods, add CSP headers in Next.js API routes |
| Middleware-Based Route Guards | High | Medium | Validate JWTs or cookies in middleware.ts, redirect or return 401 |
| Generic Error Responses | Medium | Low | Return simple messages, log details internally on server side |
| Short-Lived & Rotating Tokens | Critical | Medium | Configure session TTL, implement silent refresh and automatic rotation of refresh tokens |
By following this checklist, you can build a bulletproof authentication system that secures user data and resists common attack vectors.
Real-World Auth Patterns That Scale
As user bases expand, a basic login form can become a roadblock. For instance, startups with over 10,000 users often need authentication beyond simple email and password. By extending Supabase Auth with Next.js, you can introduce multi-stage flows similar to enterprise solutions. This design keeps speed intact while guiding users through registration, verification, and account recovery.
Multi-Step Registration And Account Verification
A Multi-Step Registration flow splits profile data, preferences, and social logins into small steps—much like a guided tour.
- Step 1: Basic user details (email, password)
- Step 2: Profile completion (avatar, display name)
- Step 3: Social provider linking (Google, GitHub)
- Step 4: Email verification via one-time token
Clear progress indicators between steps boost completion rates. Sending reminders after 24 hours helps prevent drop-offs and leads naturally into recovery patterns that complete the user lifecycle.
Password Recovery Mechanisms
Lost credentials erode trust if handled abruptly. Instead of a single reset link, offer multiple recovery paths:
- Tokenized Email Links that expire in 15 minutes
- Security Questions as a second factor
- SMS Recovery via Twilio
Each option acts like an emergency exit—if one route fails, users have another way back in. This strategy cuts support tickets by up to 70% and paves the way for smoother user management interfaces.
User Management Interfaces And State Integration
Managing users at scale involves more than a simple dashboard. Combining Supabase’s user table with Redux or Jotai lets you:
- Fetch and display paginated user lists
- Assign and modify roles with real-time updates
- Trigger webhook calls for third-party CRM sync
| Feature | Benefit | Integration Complexity | Best Practice |
|---|---|---|---|
| Role-Based Controls | Fine-grained permissions | Medium | Use Supabase RLS policies |
| Bulk User Actions | Mass invites, deletions | High | Batch RPC calls |
| Real-Time Status Indicators | Online/offline badges | Low | Leverage Supabase subscriptions |
This table highlights how each pattern balances effort and payoff, preparing you for performance tuning.
Testing Strategies And Performance Optimization
Thorough testing is essential when authentication handles large volumes. Unit tests can mock supabase.auth calls, while end-to-end suites simulate email deliveries. Key steps include:
- Automate form validation tests with Jest and React Testing Library
- Simulate expired tokens and session renewals in Cypress
- Use Lighthouse to benchmark auth page load times under 1 second
Caching session checks in memory or via Redis can cut API calls by 50%, keeping authentication snappy during peak traffic. Testing and caching strategies ensure your authentication flow remains fast and reliable as your user base grows.
Troubleshooting And Optimization: Fixing What Breaks
Even a well-configured Supabase Auth setup with Next.js can run into hiccups. Failing redirects or silent errors often point to a broken flow. Catching these issues early keeps your sign-in experience smooth and your support queue light.
Diagnosing Broken Authentication Flows
Start by inspecting your network calls in the browser’s DevTools.
- Check the 200/401 status codes on
/api/auth/*endpoints - Look at the JSON payloads for missing fields or invalid tokens
- Replay the same requests with Postman or a cURL call to isolate UI issues
For instance, a missing NEXT_PUBLIC_SUPABASE_URL value can block sign-in without any error message. Once you spot the root cause, update your environment variables or adjust your request logic to restore normal traffic.
Resolving CORS Challenges
Cross-Origin Resource Sharing (CORS) errors pop up when your front-end domain isn’t allowed.
- Set
Access-Control-Allow-Origin: https://yourdomain.comin your Next.js API routes - Whitelist only the methods you need (for example,
POST,GET,OPTIONS) - Test your calls from both secure (HTTPS) and local hosts
Treat CORS like a club with a strict guest list—only approved domains gain access, and travelers won’t end up with confusing “blocked” messages.
Managing Token Expiration
Access tokens expire by design, but sudden logouts frustrate users. To handle token expiration effectively:
- Listen to
TOKEN_REFRESHEDevents withsupabase.auth.onAuthStateChange() - Trigger a silent refresh before the token times out
- Redirect users to sign-in with a clear message if the refresh fails
Tip: Renew tokens every 25 minutes in a 30-minute TTL window. That buffer helps you avoid unexpected drops in authentication.
Session Persistence Across Navigations
Without proper storage, sessions vanish on each route change. To keep users logged in:
- Store the refresh token in an HttpOnly cookie with
SameSite=Lax - Use
@supabase/auth-helpers-nextjsin your_app.tsxfor rehydration - Validate the session on every route change via
useEffectandrouter.events
These steps ensure a page refresh doesn’t turn into a forced sign-in request.
Optimizing Performance And Caching
Repeated auth checks can slow down your pages. Caching helps cut load times:
| Technique | Load Time Impact | Complexity | Best For |
|---|---|---|---|
| In-Memory Session Cache | 30% faster | Low | Single-server deployments |
| Redis-Backed Cache | 50% faster | Medium | Multi-instance scaling |
| Static Token Validation | 20% faster | Low | High-traffic public pages |
For example, storing session data in Redis can halve your auth lookup time, letting pages render more quickly.
Maintaining Backward Compatibility During Migration
Switching from a legacy provider often means mismatched schemas and token formats. A smooth transition involves:
- Mapping old user IDs to new Supabase IDs with a migration script
- Running both JWT and Supabase sessions in parallel for 2–4 weeks
- Validating sign-in flows and role checks in a staging environment
This parallel-run strategy minimizes disruptions while you move entirely to Supabase Auth.
Main Takeaway: Fast diagnostics, strict CORS rules, timely token renewals, and smart caching are key to a reliable authentication setup.
Ready to speed up your auth integration? Try AnotherWrapper, the starter kit built with Next.js and Supabase for authentication, databases, and more. Get up and running in hours, not weeks.
Fekri




